Our Next-Generation Cyber Intelligence Platform
TITAN has long been the trusted cyber intelligence platform used by organizations across the globe to deliver Intel 471’s unparalleled insights from the cyber underground. But standing at the frontlines in the ever-evolving fight against cyber threat actors, we too must evolve if we want to continue outpacing our attackers.
We are excited to introduce Verity471, our next-generation cyber intelligence platform, that empowers you to take the lead against adversaries.
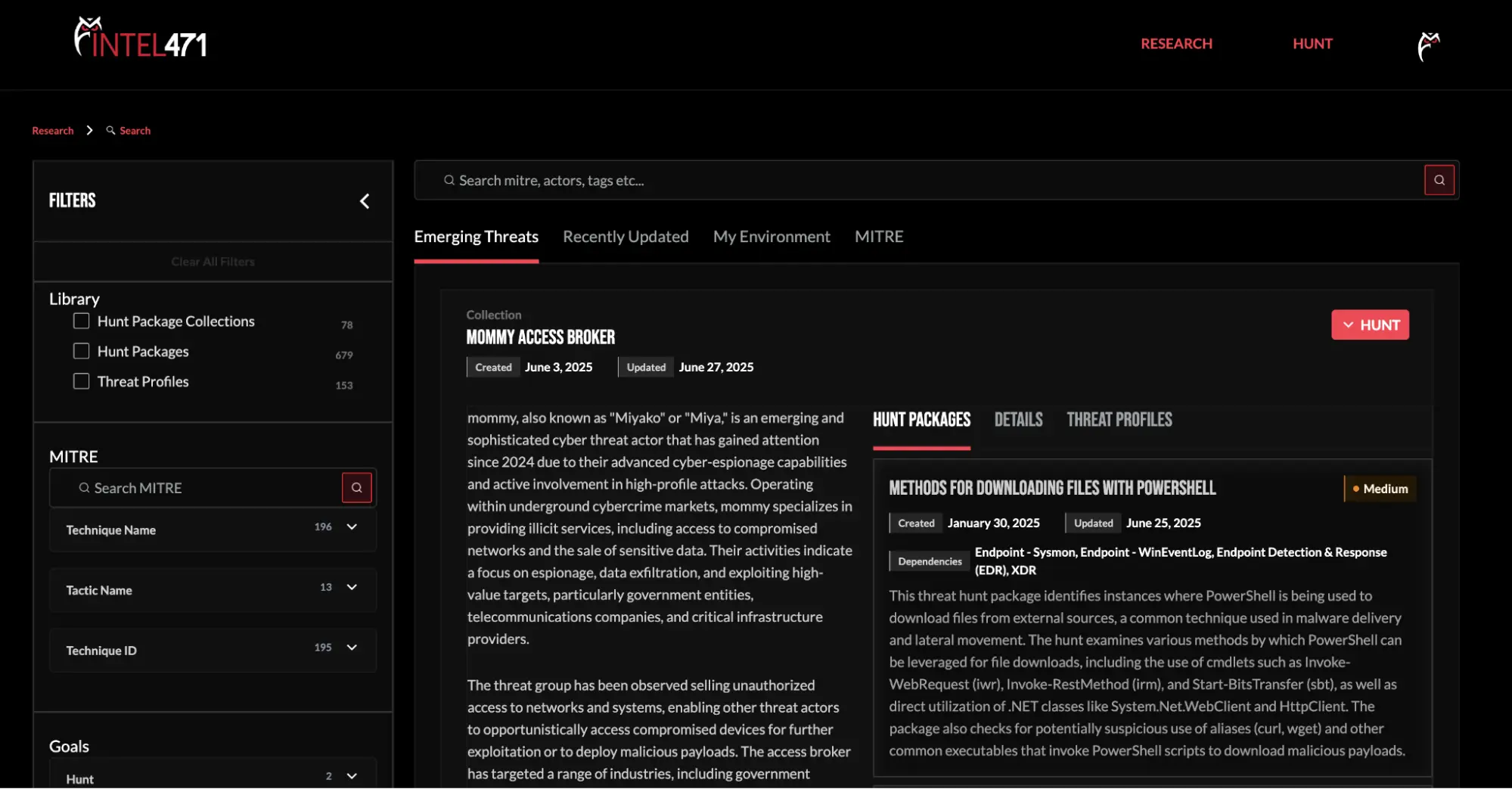
Verity471 shatters cybersecurity barriers. Pivot between prioritized attack surface exposures, actionable cyber threat intelligence, and industry-leading behavioral hunt packages, to achieve an optimal security posture.
Action the proactive power of Cyber Threat Exposure, Cyber Threat Intelligence and Cyber Threat Hunting — Verity471 unites our cyber threat portfolios within a unified cyber intelligence platform. Each of these solution portfolios will be powered by our adversary-centric cyber threat intelligence (CTI). Pivot seamlessly between prioritized attack surface exposures, exclusive CTI and industry-leading behavioral hunt packages to identify, mitigate and neutralize cyber threats. Verity471 will deliver cyber threat insights enriched with context and ready for action, all at your fingertips.
Verity471 integrates with your existing tools and systems, enabling the rapid dissemination of intelligence across your cybersecurity ecosystem. Shatter the cycle of reacting to threats and take the lead against your adversaries with a faster, more-informed response to cyber threats.
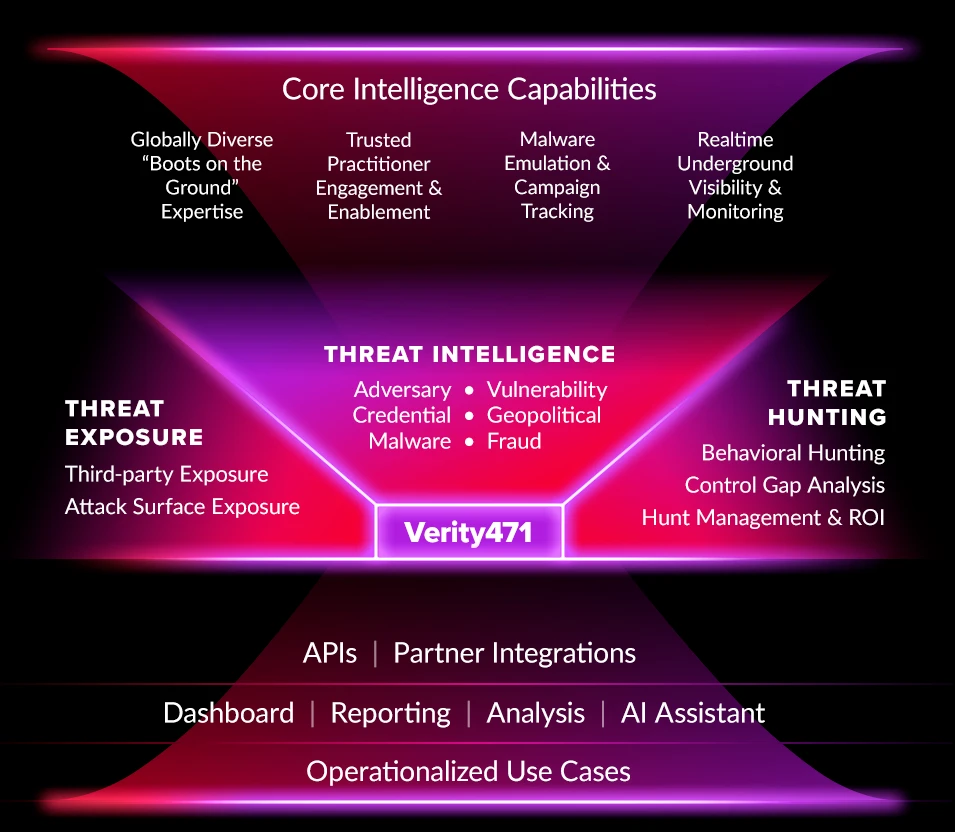
Verity471 is purpose‑built to operationalize our leading cyber threat intelligence out of the box, bringing together our three core portfolios — Cyber Threat Exposure, Cyber Threat Intelligence, and Cyber Threat Hunting — into a single, unified platform.
The Verity471 platform is built for transforming intelligence into action, and provides:
A Unified Foundation: Pivot seamlessly between modes for Cyber Threat Exposure, Cyber Threat Intelligence and Cyber Threat Hunting to streamline workflows and accelerate investigations.
Actionable Intelligence for a Proactive Defense: Each mode is fuelled by our CTI providing the analysis of threat actor behaviour needed for better patch prioritization, to harden defenses against anticipated attacks and refine threat hunts to more effectively identify and neutralize undetected threats within your environment.
A Cohesive Image of Your Threat Landscape: Continuous monitoring of threat actors, graph visualizations and extensive drill-down capabilities to support deep investigation of threats.
Enabled Collaboration and Dissemination: Build and monitor watchers collaboratively, and share intelligence across stakeholders with integrated APIs and AI-assisted reporting to streamline workflows and align CTI output with strategic goals.
Intuitive User-experience: Enhanced searches, near real-time alerts and dashboards surfacing high-priority insights for faster, informed decision making.
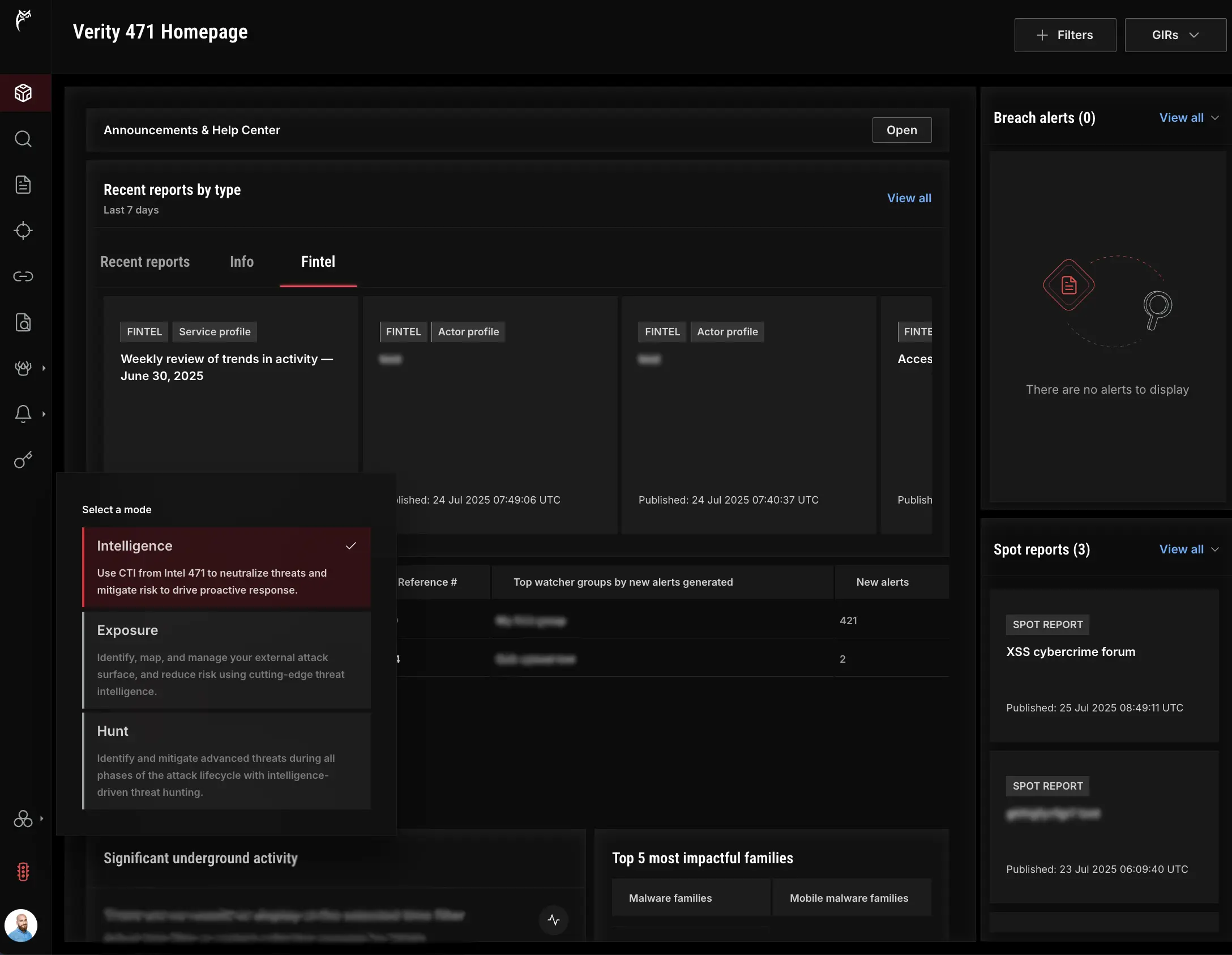
Access our portfolios on Verity471 through three modes that empower organizations to unlock solutions to your growing use cases.
With Verity471, security teams can effortlessly pivot between Intel 471’s core intelligence solution portfolios through a specific mode: Exposure, Intelligence and Hunt. Each is powered by Intel 471’s industry leading cyber threat intelligence (CTI).
Intel 471’s industry leading CTI is the cornerstone of each mode meaning Verity471 is built to surface new and actionable insights across your enterprise. Teams can prioritize high-risk exposures mapped to cyber threats tracked by Intel 471’s global team of intelligence analysts.
Timely CTI equips security teams to operationalize our behavioral hunt packages to identify advanced and undetected threats inside your environment. The platform provides the ultimate intelligence-driven tools to help your organization maximize its return on security investments, measure CTI and hunt success metrics, and drive improvements to your security posture.
SEE
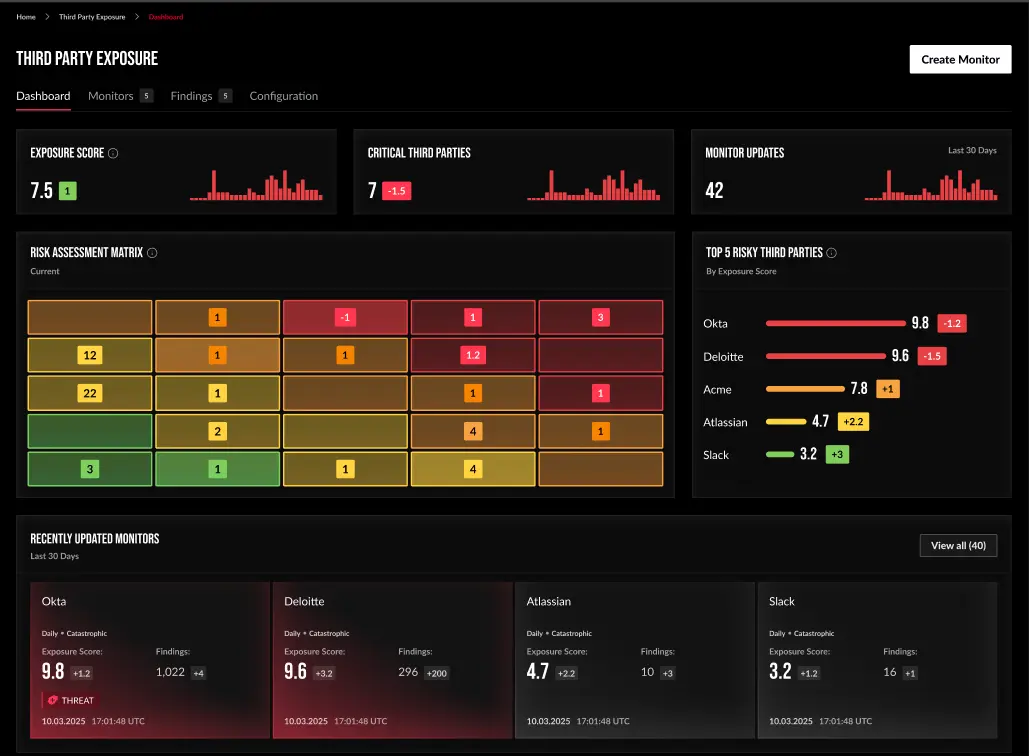
See your attack surface through an attacker’s eyes. Discover and prioritize exposures within your external attack surface and mitigate your exposure to third parties using Intel 471’s unmatched CTI data.
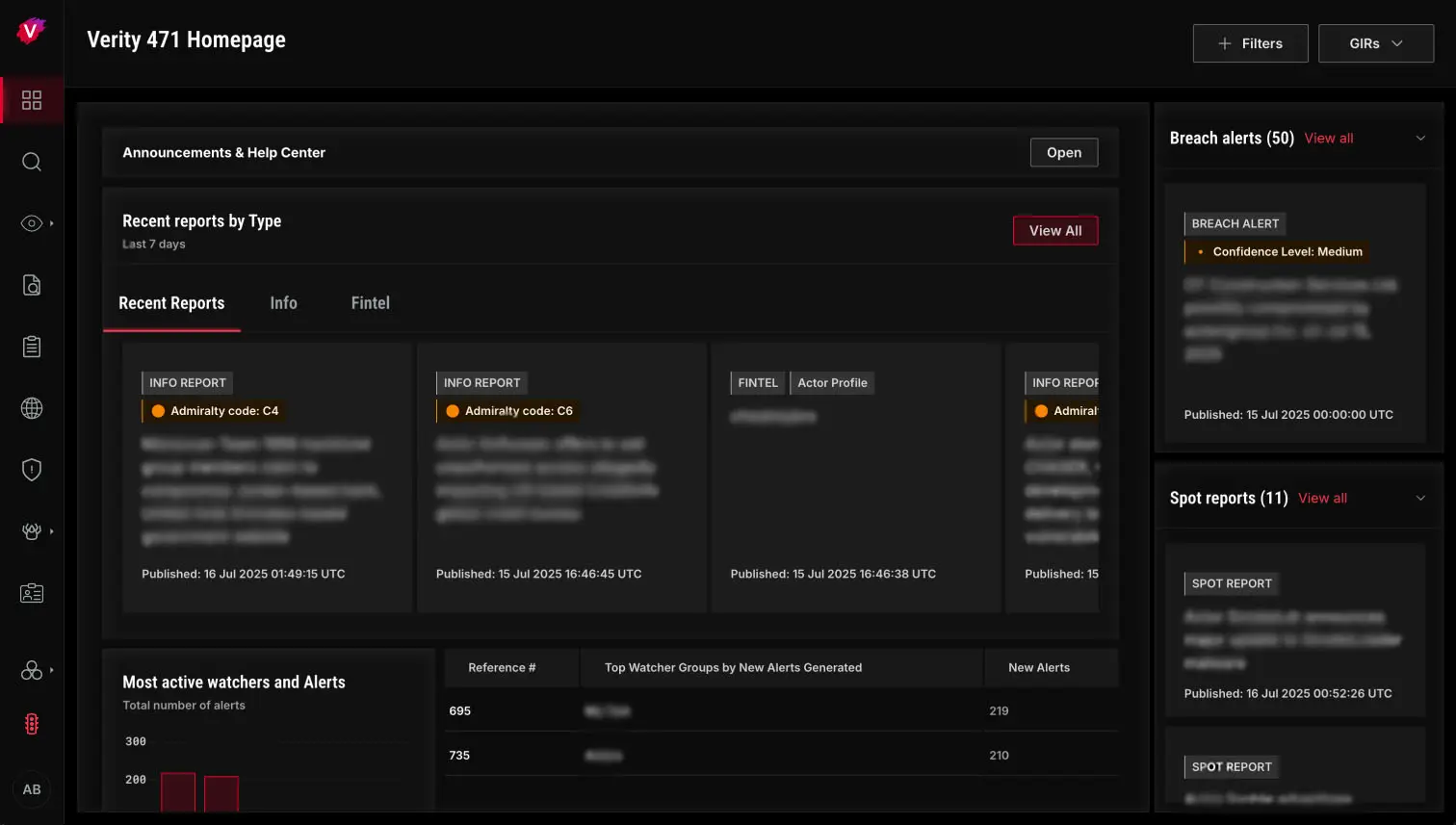
KNOW
Know your adversary. Gain true cyber threat actor insight through expert human intelligence (HUMINT), deep malware emulation, and automated collection. Intel 471 helps you pre-empt attackers by unveiling cyber threats emerging from malware, compromised credentials, vulnerabilities, and more.
NEUTRALIZE
Neutralize emerging threats before retroactive detections ever trigger an alarm. Reduce attack dwell time by proactively hunting for adversary behaviors and their evolving tactics, techniques, and procedures—using pre-validated behavioral hunt packages crafted by our world-class threat hunters.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.